
Introduction
Blockchain technology has redefined digital trust by enabling decentralized, tamper-resistant ledgers for cryptocurrencies, smart contracts, and more. However, the rise of quantum computing introduces new security challenges. Quantum computers, with their immense computational power, have the potential to break the cryptographic algorithms that underpin blockchain security. Understanding this intersection is vital for developers, organizations, and anyone invested in the future of secure, decentralized systems.
1. How Quantum Computing Threatens Blockchain Security
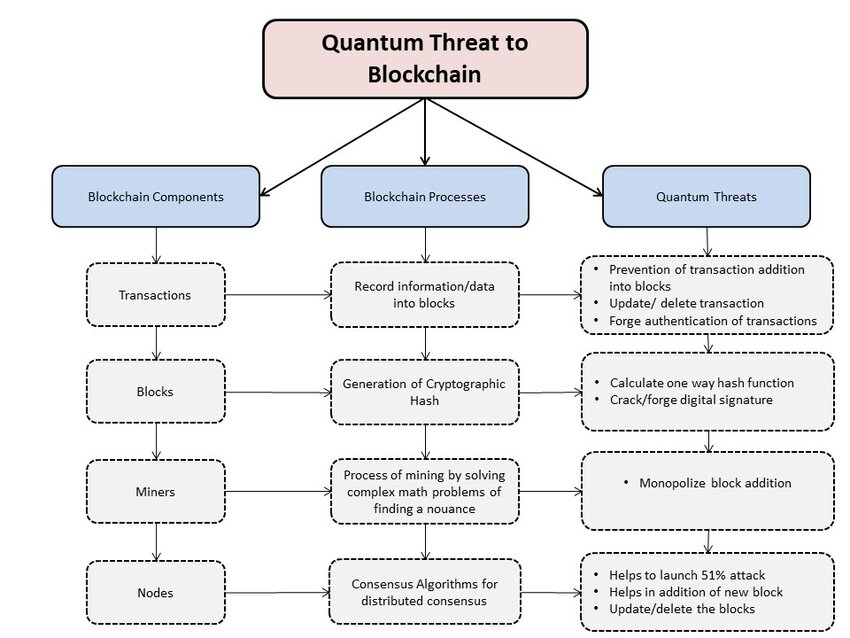
Quantum computers can solve certain mathematical problems exponentially faster than classical computers. This capability poses two significant threats to blockchain security:
A. Breaking Digital Signatures
Blockchains rely heavily on asymmetric cryptography—such as RSA and ECDSA—for digital signatures that authenticate transactions and verify user identities. Quantum algorithms like Shor’s can efficiently factor large numbers and compute discrete logarithms, making it possible for a quantum attacker to derive private keys from public keys. This could allow attackers to forge transactions, steal assets, and compromise the integrity of blockchain networks.
B. Weakening Hash Functions
Blockchains use cryptographic hash functions (like SHA-256) to secure data integrity and validate blocks. Quantum algorithms such as Grover’s can speed up the search for hash collisions or pre-images, potentially making it easier to find two different inputs that produce the same hash or to reverse-engineer a hash. This could enable attackers to manipulate transaction records or disrupt consensus mechanisms.
2. Real-World Risks and Current State
- Cryptocurrency Vulnerability: Billions of dollars in cryptocurrencies and digital assets could be at risk if quantum computers become powerful enough to break existing cryptographic protections. A significant portion of current Bitcoins, for example, are vulnerable if stored in older, less secure address formats.
- Consensus Mechanisms: Quantum computers could undermine consensus protocols, such as proof-of-work, by accelerating mining or manipulating block validation, threatening the fairness and security of the network.
- Smart Contracts and DApps: Quantum threats extend to smart contracts and decentralized applications, which depend on secure cryptographic primitives for execution and trust.
3. Mitigation Strategies: Building Quantum-Resistant Blockchains
A. Post-Quantum Cryptography (PQC)
Transitioning to quantum-resistant cryptographic algorithms is the primary defense. PQC algorithms, such as lattice-based, hash-based, and multivariate polynomial schemes, are designed to withstand attacks from both classical and quantum computers. Many blockchain projects are actively researching and piloting these algorithms to future-proof their networks.
B. Quantum Key Distribution (QKD)
QKD uses quantum mechanics to securely exchange encryption keys. Any attempt at eavesdropping is detectable, providing a layer of security fundamentally different from traditional cryptography. While QKD is promising, it currently requires specialized hardware and is best suited for high-value or critical infrastructure.
C. Quantum Random Number Generators (QRNGs)
True randomness is essential for cryptographic strength. QRNGs use quantum phenomena to generate unpredictable random numbers, enhancing the security of keys, wallets, and consensus protocols.
D. Hybrid Cryptographic Approaches
During the transition, hybrid schemes that combine classical and quantum-resistant algorithms can provide layered security, ensuring resilience even as standards evolve.
4. Steps for Blockchain Developers and Organizations
- Assess Cryptographic Dependencies: Inventory all cryptographic mechanisms in use, from wallet generation to consensus and smart contract execution.
- Pilot Quantum-Safe Solutions: Begin integrating and testing PQC algorithms in non-critical systems, and collaborate with the broader blockchain and cryptography communities.
- Upgrade Protocols and Infrastructure: Plan for updates to hashing algorithms, digital signature schemes, and network protocols to support quantum resistance.
- Educate and Train Teams: Ensure developers and security personnel understand quantum risks and the importance of quantum-safe practices.
- Monitor Standards and Research: Stay updated with developments from global standards bodies and research initiatives focused on quantum-safe blockchain technologies.
5. Quantum-Enhanced Blockchain Opportunities
While quantum computing poses threats, it also offers opportunities for blockchain innovation:
- Quantum-Secure Consensus Protocols: New consensus mechanisms can be designed to resist quantum attacks, leveraging quantum-resistant cryptographic primitives.
- Quantum Key Distribution Integration: QKD can be used to secure communication channels between blockchain nodes, making the network more resilient to attacks.
- Enhanced Privacy and Zero-Knowledge Proofs: Quantum computing could enable more efficient and private transaction validation, further strengthening blockchain privacy features.
6. The Road Ahead
Quantum computing is still in its early stages, but proactive preparation is essential. The blockchain community is already taking steps to develop quantum-resistant solutions, collaborating across disciplines to identify vulnerabilities and build robust defenses. The future of blockchain security will depend on the successful integration of quantum-safe technologies, continuous research, and industry-wide cooperation.
Conclusion
The intersection of quantum computing and blockchain security is both a challenge and an opportunity. While quantum computers threaten the cryptographic foundations of blockchain, they also inspire the development of more advanced, resilient security measures. By embracing quantum-resistant cryptography, exploring quantum-enhanced technologies, and fostering collaboration, the blockchain ecosystem can remain secure and trustworthy in the quantum era.