
Introduction
Quantum computing is poised to revolutionize industries with its unparalleled processing capabilities. However, it also introduces a new category of cyber threats, as quantum algorithms could break many of the cryptographic systems that currently secure sensitive data. For organizations, preparing for quantum threats is not just a technical upgrade—it’s a strategic imperative. This tutorial provides a step-by-step guide for organizations to assess risk, implement quantum-safe practices, and future-proof their security infrastructure.
1. Understand the Quantum Threat Landscape
Quantum computers leverage quantum mechanics to solve certain mathematical problems exponentially faster than classical computers. Algorithms like Shor’s can efficiently factor large numbers, threatening public-key cryptosystems such as RSA, ECC, and DH. This means that once quantum computers reach sufficient scale, encrypted data protected by these systems could be decrypted, exposing confidential information.
2. Inventory and Assess Cryptographic Assets
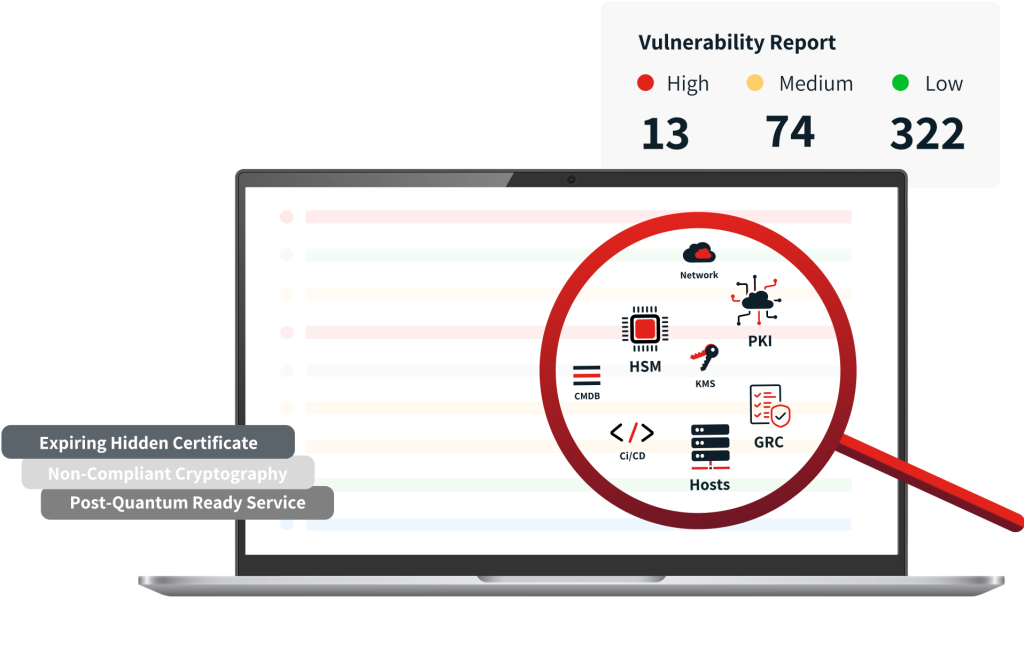
- Catalog All Cryptographic Usage: Identify where cryptography is used across your organization—data storage, communications, authentication, and third-party integrations.
- Classify Data Sensitivity: Determine which data is most sensitive or has a long shelf life, as this information is at greatest risk from “harvest now, decrypt later” attacks.
- Evaluate Legacy Systems: Note any systems that are difficult to update or replace, as these may require special attention during the transition.
3. Develop a Quantum-Safe Migration Strategy
- Adopt Cryptographic Agility: Ensure your systems can support rapid updates or replacements of cryptographic algorithms as new standards emerge.
- Pilot Post-Quantum Cryptography (PQC): Begin testing and integrating quantum-resistant algorithms, such as lattice-based or hash-based cryptography, in non-critical systems.
- Hybrid Approaches: Use a combination of classical and quantum-safe algorithms during the transition period to maintain layered security.
4. Update Procurement and Infrastructure Policies
- Quantum-Ready Hardware and Software: When acquiring new technology, prioritize solutions that support quantum-safe cryptography or can be easily upgraded.
- Patch Management: Maintain a robust patching process to ensure quick adoption of security updates and cryptographic improvements.
5. Strengthen Governance and Risk Management
- Integrate Quantum Risk into Enterprise Risk Management: Make quantum threats a formal part of your risk assessments and governance processes.
- Develop a Phased Roadmap: Set clear milestones for awareness, transition, and full adoption of quantum-safe measures, regularly reviewing progress.
6. Educate and Train Teams
- Awareness Programs: Inform leadership and staff about quantum risks and the importance of preparing now.
- Technical Training: Upskill IT and security teams on quantum-safe cryptography, new protocols, and migration strategies.
7. Collaborate and Stay Informed
- Engage with Vendors and Partners: Work closely with technology partners to ensure their solutions are quantum-ready and to coordinate migration timelines.
- Monitor Standards and Research: Stay updated with developments from organizations like NIST and participate in industry forums to learn about best practices and new threats.
8. Implement Defense-in-Depth
- Layered Security: Combine quantum-resistant cryptography with strong access controls, network segmentation, and monitoring tools to provide multiple lines of defense.
- Focus on Data in Transit: Prioritize securing communications channels, as these are often the first targets for interception.
9. Test, Validate, and Simulate
- Conduct Regular Security Audits: Test your quantum-safe implementations and simulate attack scenarios to identify weaknesses.
- Continuous Improvement: Use findings from audits and simulations to refine your quantum readiness strategy.
10. Plan for Long-Term Resilience
- Future-Proof Policies: Build flexibility into your security policies so they can adapt as quantum computing and cryptography evolve.
- Ongoing Review: Regularly revisit your quantum threat strategy to ensure it remains aligned with technological advances and organizational needs.
Conclusion
Quantum threats are inevitable, but organizations that act now can ensure their data and operations remain secure. By understanding the risks, inventorying assets, adopting quantum-safe cryptography, updating infrastructure, strengthening governance, educating teams, collaborating with partners, and implementing layered defenses, organizations can stay ahead of the quantum curve. Proactive preparation today is the foundation for resilient cybersecurity in the quantum era.