
Introduction
Quantum computing is no longer a distant possibility—it is an emerging reality that promises to disrupt industries and revolutionize technology. However, this power comes with a significant risk: quantum computers will be able to break many of today’s widely used cryptographic systems, exposing sensitive data to new threats. Quantum-safe encryption, also known as post-quantum or quantum-resistant encryption, is essential to protect information in the quantum era. This comprehensive tutorial explores the technologies behind quantum-safe encryption, strategies for implementation, and practical steps for organizations to secure their digital assets against future quantum attacks.
1. Understanding Quantum-Safe Encryption
Quantum-safe encryption refers to cryptographic methods that remain secure even in the presence of quantum computers. Unlike traditional algorithms that rely on the difficulty of problems like factoring large numbers or computing discrete logarithms, quantum-safe encryption is based on mathematical problems believed to be hard for both classical and quantum computers. The goal is to ensure that even as quantum technology advances, encrypted data remains protected.
2. Core Technologies in Quantum-Safe Encryption
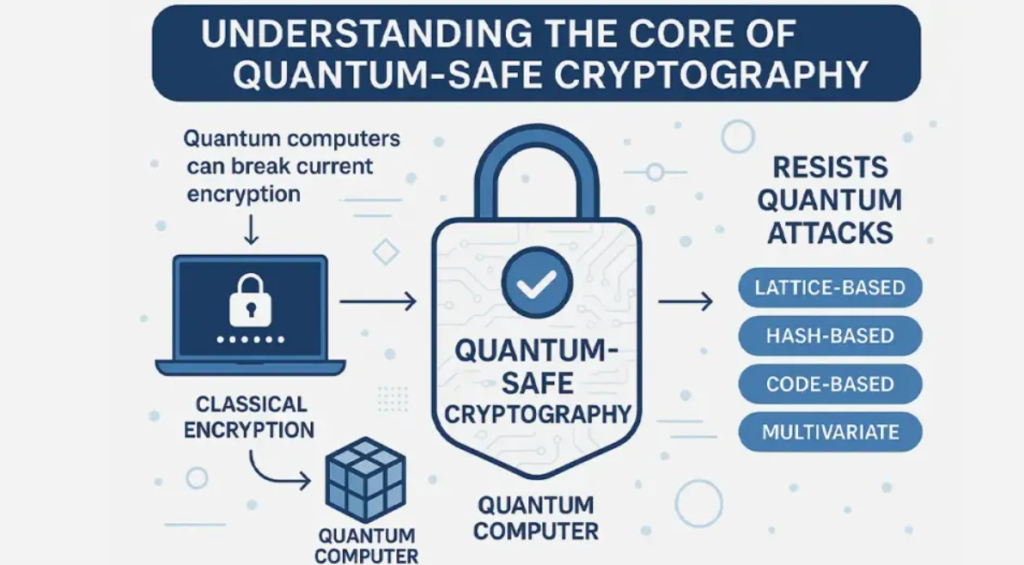
A. Post-Quantum Cryptography (PQC)
PQC consists of algorithms designed to resist attacks from both classical and quantum computers. Key families include:
- Lattice-Based Cryptography: Relies on hard problems in lattice mathematics, such as Learning With Errors (LWE). Algorithms like Kyber and Dilithium have been standardized for their strong security and efficiency.
- Hash-Based Cryptography: Uses hash functions for digital signatures, offering simplicity and robust security. These are especially useful for signing software and securing firmware updates.
- Code-Based Cryptography: Employs error-correcting codes, as seen in the McEliece cryptosystem, which has withstood decades of cryptanalysis.
- Multivariate Polynomial Cryptography: Based on the difficulty of solving systems of multivariate equations.
- Supersingular Isogeny-Based Cryptography: Uses advanced mathematics involving elliptic curves, though it remains under active research.
B. Quantum Key Distribution (QKD)
QKD uses the laws of quantum physics to securely distribute encryption keys. Its security is guaranteed by fundamental principles such as the no-cloning theorem and the Heisenberg uncertainty principle. Any attempt to eavesdrop on a quantum channel introduces detectable disturbances, alerting the communicating parties to potential threats. QKD is ideal for high-security applications and is already being deployed in critical sectors.
C. Quantum Random Number Generators (QRNGs)
True randomness is critical for secure encryption. QRNGs use quantum phenomena to generate unpredictable random numbers, strengthening the cryptographic keys used in both classical and quantum-safe systems.
3. Strategies for Implementing Quantum-Safe Encryption
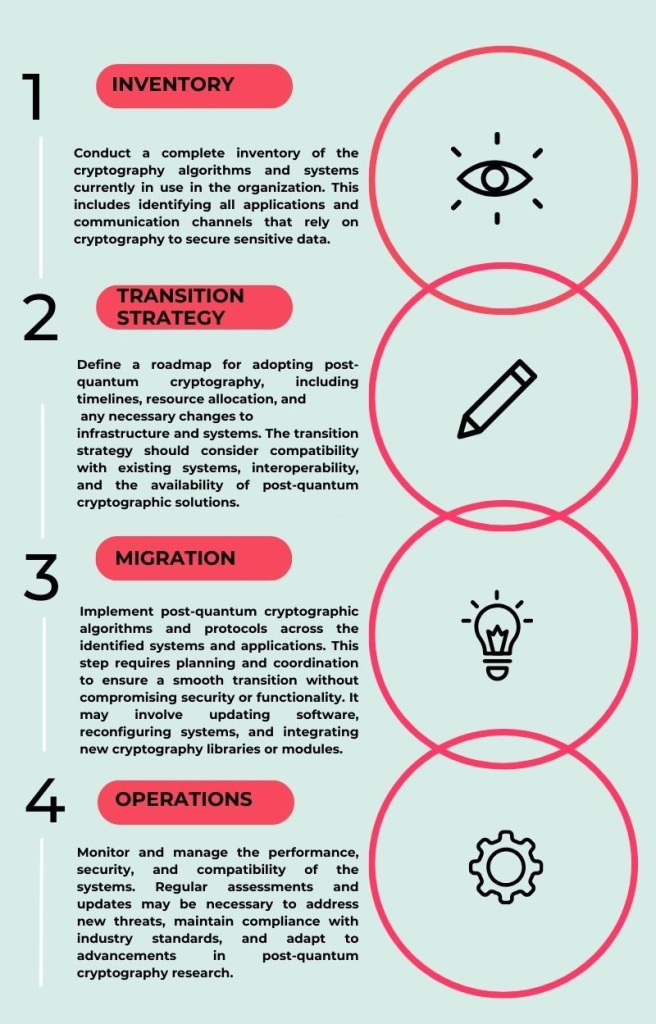
Step 1: Inventory and Assess Cryptographic Assets
- Catalog all systems and applications using cryptography, from data storage to communications and authentication.
- Identify sensitive and long-lived data that must be prioritized for quantum-safe protection.
Step 2: Adopt Crypto-Agility
- Design systems to support rapid updates or replacements of cryptographic algorithms as new standards emerge.
- Use modular architectures that allow easy swapping of algorithms without major system overhauls.
Step 3: Begin Transitioning to PQC Algorithms
- Test and integrate standardized PQC algorithms in non-critical systems to evaluate performance and compatibility.
- Use hybrid cryptography, combining classical and quantum-safe algorithms, during the transition to maintain layered security.
Step 4: Upgrade Hardware Security Modules (HSMs)
- Ensure your HSMs can support PQC algorithms and can be updated as standards evolve, enabling secure key management in the quantum era.
Step 5: Collaborate and Stay Informed
- Engage with vendors and industry partners to ensure their solutions are quantum-ready.
- Monitor standards from organizations such as NIST and participate in industry forums to stay updated on best practices and emerging threats.
Step 6: Plan for Long-Term Resilience
- Develop a phased roadmap for quantum-safe migration, including pilot projects, full-scale deployment, and ongoing review.
- Regularly test and validate quantum-safe implementations through security audits and simulations.
4. Challenges and Considerations
- Performance and Compatibility: PQC algorithms may require more processing power and larger key sizes than classical algorithms. Test thoroughly on all platforms, especially resource-constrained devices.
- Legacy Systems: Some older systems may be difficult to update. Develop risk-managed approaches, such as using quantum-safe VPNs to protect legacy traffic.
- Regulatory Compliance: Stay ahead of evolving regulations and standards to ensure compliance and avoid costly retrofits.
5. Practical Example: Lattice-Based Encryption
Overview:
Lattice-based cryptography is one of the most promising quantum-safe approaches. For example, the Kyber algorithm is used for key encapsulation, while Dilithium is used for digital signatures. Both are efficient and have been standardized for use in quantum-safe systems.
Implementation Steps:
- Choose a cryptographic library that supports PQC algorithms.
- Integrate Kyber for secure key exchange and Dilithium for digital signatures in your applications.
- Test the system for compatibility, performance, and security.
- Transition gradually, using hybrid solutions where necessary, to ensure a smooth migration.
6. The Road Ahead
Quantum-safe encryption is not a one-time upgrade but an ongoing journey. As quantum computing progresses, organizations must remain vigilant, agile, and proactive. Early adoption of quantum-safe technologies, combined with continuous education and collaboration, will ensure long-term data protection and regulatory compliance.
Conclusion
Quantum-safe encryption is essential for securing data in the quantum era. By understanding the underlying technologies, adopting crypto-agile strategies, and staying engaged with ongoing developments, organizations can protect their digital assets against both current and future threats. The transition to quantum-safe encryption is not just a technical necessity—it is a strategic imperative for maintaining trust, compliance, and competitive advantage in a rapidly evolving digital world.