
Introduction
As quantum computing advances, traditional cryptographic defenses are increasingly at risk. Quantum Key Distribution (QKD) stands out as a revolutionary technology, harnessing the principles of quantum mechanics to enable secure communication. Unlike classical encryption, QKD offers a fundamentally new way to distribute cryptographic keys, ensuring data privacy even in the face of powerful quantum computers.
1. What Is Quantum Key Distribution?
Quantum Key Distribution is a method of securely exchanging cryptographic keys between two parties by using quantum mechanics. The security of QKD is not based on computational complexity, but on the fundamental laws of physics. If an eavesdropper tries to intercept the key, the quantum state of the particles used to transmit the key is disturbed, making the interception immediately detectable.
2. Quantum Principles Behind QKD
- No-Cloning Theorem: It is impossible to create an identical copy of an arbitrary quantum state. This means any attempt to intercept or clone the quantum key will introduce detectable errors.
- Heisenberg Uncertainty Principle: Measuring certain quantum properties disturbs them, so eavesdropping on a quantum channel changes the transmitted information in a way that can be detected.
- Quantum Randomness: QKD leverages the inherent unpredictability of quantum events, ensuring that the generated keys are truly random and highly secure.
3. How Does QKD Work? Step-by-Step Tutorial
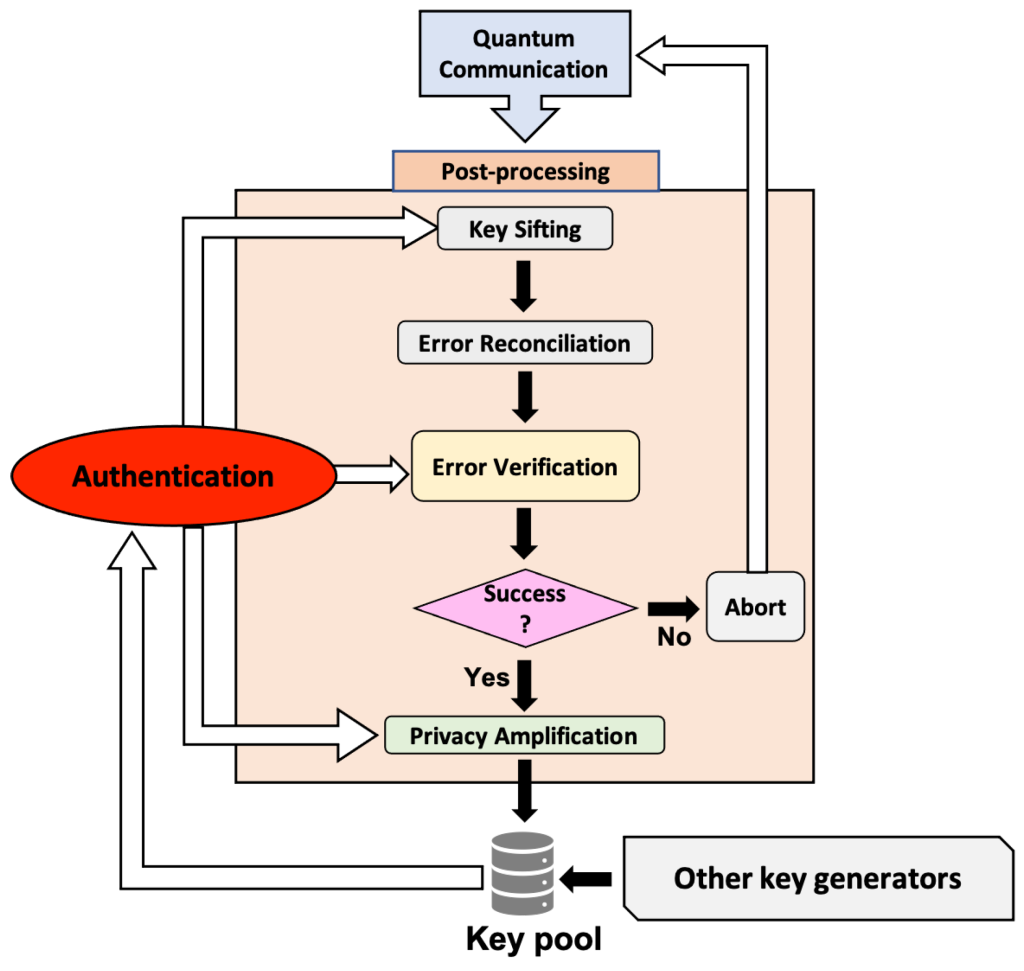
The BB84 Protocol
The BB84 protocol, developed in 1984, is the foundational QKD protocol and remains widely used.
Step 1: Preparation and Encoding
- The sender (often called Alice) encodes bits of the key onto quantum particles, typically photons.
- Two sets of polarization bases are used (rectilinear and diagonal), with each bit randomly assigned a basis and value.
Step 2: Transmission
- Alice sends the encoded photons over a quantum channel (fiber optic cable or free space) to the receiver (Bob).
Step 3: Measurement
- Bob randomly selects a basis for each incoming photon and measures its polarization.
Step 4: Sifting
- Alice and Bob publicly compare the bases they used (not the actual bit values).
- They keep only the bits where their bases matched, discarding the rest.
Step 5: Error Correction
- Alice and Bob perform error correction to reconcile any discrepancies due to noise or potential eavesdropping.
Step 6: Privacy Amplification
- They apply privacy amplification techniques to remove any bits that may have been compromised, resulting in a shorter but highly secure shared key.
4. Security Benefits of QKD
- Eavesdropping Detection: Any interception attempt introduces errors, alerting the communicating parties to possible security breaches.
- Unconditional Security: Security is based on the laws of quantum physics, not on assumptions about computational hardness.
- Quantum Randomness: The keys generated are truly random, making them immune to prediction or brute-force attacks.
5. Real-World Applications and Use Cases
- Government and Military: Securing top-secret communications and critical infrastructure.
- Financial Services: Protecting sensitive financial transactions and data transfers.
- Healthcare: Safeguarding patient records and confidential medical data.
- Telecommunications: Ensuring privacy in high-value data transmissions across networks.
6. Challenges and Limitations
- Infrastructure Requirements: QKD requires specialized hardware and quantum channels, which can be costly and complex to deploy.
- Distance Limitations: Quantum signals can degrade over long distances, requiring repeaters or satellites for global coverage.
- Integration: Integrating QKD with existing classical cryptographic systems and networks is an ongoing area of research and development.
- Scalability: Widespread adoption is currently limited to high-security environments due to cost and technical constraints.
7. The Future of QKD
As research and technology progress, QKD is expected to become more accessible and cost-effective. Innovations such as satellite-based QKD and quantum repeaters are expanding its reach. While QKD may not replace all classical cryptography, it will play a crucial role in securing the most sensitive communications in the quantum age.
Conclusion
Quantum Key Distribution represents a paradigm shift in cybersecurity. By leveraging the fundamental principles of quantum mechanics, QKD provides a level of security that is unattainable with classical methods. As quantum threats become more real, organizations and governments must consider QKD for their most critical data and communications, ensuring robust protection in the quantum era.