
Introduction
The dawn of quantum computing is set to transform the digital landscape, promising breakthroughs in science, optimization, and artificial intelligence. However, this quantum revolution also brings a significant challenge: the potential to break the cryptographic systems that currently safeguard our data and communications. Post-quantum cryptography (PQC) emerges as the solution, focusing on developing algorithms that remain secure even against the immense power of quantum computers. This tutorial provides a thorough understanding of PQC, its importance, the mathematics behind it, and practical steps for organizations and individuals to prepare for the quantum age.
1. Why Post-Quantum Cryptography Is Essential
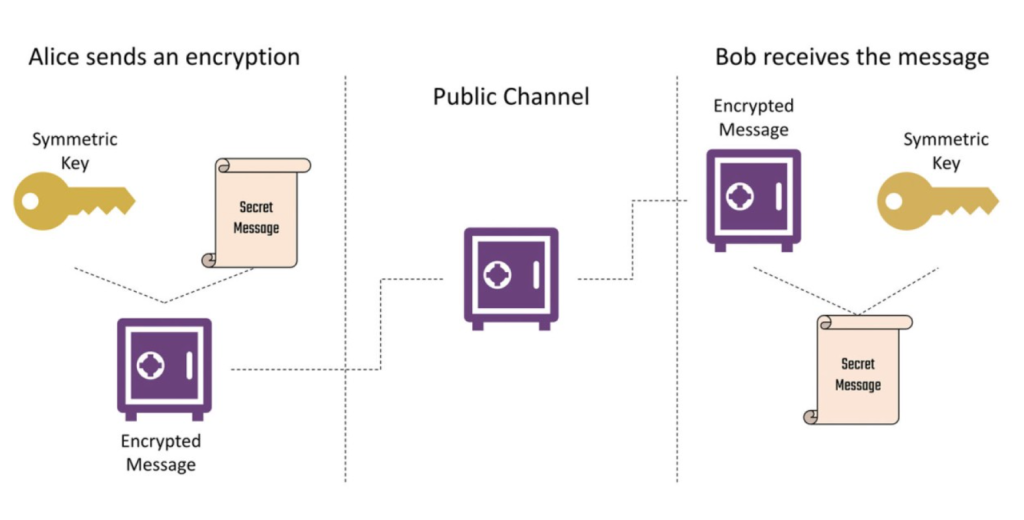
The Quantum Threat
Quantum computers operate fundamentally differently from classical computers. While classical systems use bits (0 or 1), quantum computers use qubits, which can exist in multiple states at once due to superposition and entanglement. This unique capability allows quantum computers to solve certain mathematical problems—like factoring large numbers and computing discrete logarithms—exponentially faster than classical computers.
Impact on Current Cryptography
Most of today’s widely used cryptographic systems, such as RSA, Diffie-Hellman, and elliptic curve cryptography, rely on the difficulty of these mathematical problems. Quantum algorithms, particularly Shor’s algorithm, can efficiently solve them, rendering these systems vulnerable. This means that once quantum computers become powerful enough, encrypted data protected by these algorithms could be decrypted, exposing sensitive information.
Harvest Now, Decrypt Later
A major concern is that attackers may already be collecting encrypted data with the intention of decrypting it in the future, once quantum computers are available. This makes it urgent to transition to quantum-resistant cryptography now, to protect both current and future data.
2. Core Principles of Post-Quantum Cryptography
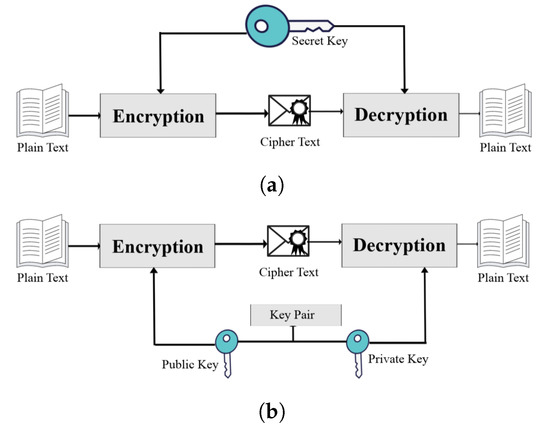
What Is PQC?
Post-quantum cryptography refers to cryptographic algorithms designed to be secure against both classical and quantum attacks. Unlike quantum cryptography, which uses quantum mechanics for secure communication, PQC is based on mathematical problems believed to be hard even for quantum computers. These algorithms can be implemented on today’s classical hardware and networks.
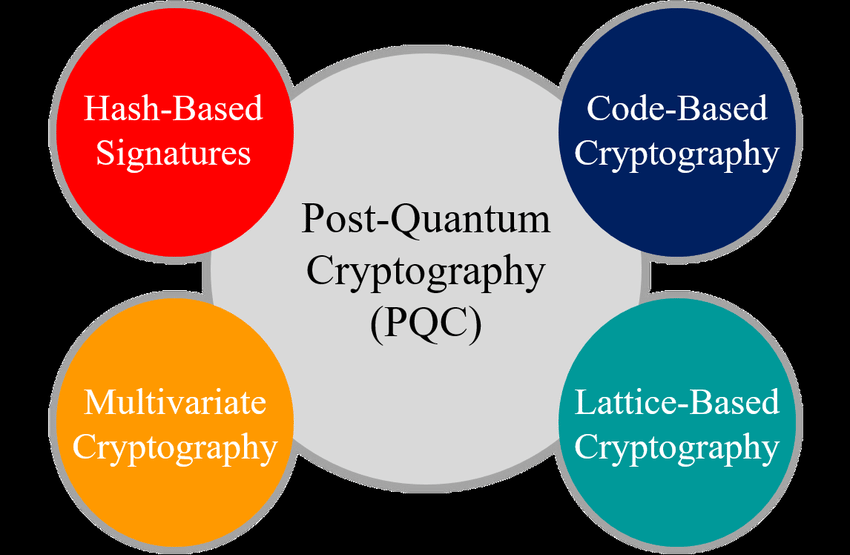
Main Families of PQC Algorithms:
- Lattice-Based Cryptography: Relies on the hardness of lattice problems, such as the Shortest Vector Problem (SVP) and Learning With Errors (LWE). These are currently considered resistant to quantum attacks and are leading candidates for standardization.
- Code-Based Cryptography: Uses error-correcting codes as the basis for security. The McEliece cryptosystem is a well-known example.
- Hash-Based Cryptography: Employs hash functions for digital signatures. These are simple, well-understood, and offer strong security guarantees.
- Multivariate Polynomial Cryptography: Based on the difficulty of solving systems of multivariate polynomial equations.
- Supersingular Isogeny-Based Cryptography: Uses the mathematics of elliptic curve isogenies. This area is still under active research.
3. Standardization and Global Efforts
NIST and International Collaboration
The National Institute of Standards and Technology (NIST) has led a global effort to evaluate and standardize post-quantum cryptographic algorithms. Since 2016, experts worldwide have analyzed and tested candidate algorithms for security, efficiency, and practicality. In 2024, NIST released the first final standards, marking a major milestone in the journey toward quantum-safe security.
Why Standardization Matters
Standardization ensures that the new algorithms are robust, interoperable, and suitable for widespread adoption. It also provides guidance for governments, businesses, and technology providers to begin the migration process.
4. Practical Steps for Organizations and Developers
1. Inventory and Assessment
- Identify where cryptography is used within your organization (data storage, communications, authentication, etc.).
- Assess which systems rely on algorithms vulnerable to quantum attacks.
2. Planning for Migration
- Develop a roadmap for transitioning to PQC, prioritizing critical systems and sensitive data.
- Stay updated on the latest standards and recommendations from NIST and other authorities.
3. Implementation
- Begin testing and integrating PQC algorithms in non-critical systems first.
- Ensure that new solutions are compatible with existing infrastructure.
- Consider hybrid approaches that combine classical and quantum-resistant algorithms during the transition period.
4. Performance and Security Testing
- Evaluate the performance of PQC algorithms, especially on devices with limited resources (such as IoT and embedded systems).
- Conduct thorough security assessments to ensure no new vulnerabilities are introduced.
5. Training and Awareness
- Educate teams about the quantum threat and the importance of PQC.
- Stay engaged with the cryptographic community to track advancements and best practices.
5. PQC vs. Quantum Cryptography
Post-Quantum Cryptography:
- Based on hard mathematical problems.
- Can be implemented on classical computers and networks.
- Does not require specialized quantum hardware.
Quantum Cryptography (e.g., Quantum Key Distribution):
- Uses quantum mechanics to secure communication channels.
- Requires quantum hardware and infrastructure.
- Offers information-theoretic security but is currently limited in scalability and practicality.
6. Challenges and Future Directions
Technical and Operational Hurdles
- PQC algorithms often have larger key sizes and higher computational requirements than classical algorithms.
- Updating legacy systems and protocols can be complex and resource-intensive.
- Ensuring backward compatibility and smooth migration is critical.
Ongoing Research
- Continuous cryptanalysis is essential to validate the security of PQC algorithms.
- Research into optimizing algorithms for efficiency and practicality is ongoing.
- Collaboration between academia, industry, and government is crucial for successful adoption.
7. Hands-On Tutorial: Getting Started with PQC
Step 1: Explore Open-Source Libraries
- Many cryptographic libraries now include experimental PQC algorithms. Examples include OpenSSL (with PQC extensions), liboqs, and PQCrypto.
Step 2: Test PQC Algorithms
- Try implementing lattice-based encryption (like Kyber) or hash-based signatures (like SPHINCS+) in a test environment.
- Evaluate encryption, decryption, signature generation, and verification performance.
Step 3: Hybrid Cryptography
- Combine PQC algorithms with classical algorithms to ensure compatibility and security during the transition.
Step 4: Monitor Developments
- Stay informed about new standards, vulnerabilities, and best practices as the field evolves.
Conclusion
Quantum computing is both an opportunity and a challenge for the digital world. While it promises transformative advances, it also necessitates a fundamental shift in how we secure our data. Post-quantum cryptography is the proactive response, ensuring that our digital infrastructure remains safe in the face of quantum-powered adversaries. By understanding the principles, preparing for migration, and staying engaged with ongoing research, organizations and individuals can confidently navigate the transition to the quantum age.